mohanshtechnologies is the best online bootcamp provider that enables learners through rigorous and highly specialized training. We focus on emerging technologies and processes that are transforming the digital world, at a fraction of the cost and time as traditional approaches. Serves as a global authentication authority that allows employees, customers and partners to securely access all the applications they need from any device.

An Expert, A systematic educational course called an ethical hacking training program aims to provide students with the abilities and information needed to work as ethical hackers or cybersecurity specialists. Penetration testing, white-hat hacking, and ethical hacking are terms used to describe the practice of simulating cyberattacks on computer systems, networks, and applications in order to find vulnerabilities and flaws before malevolent hackers may take advantage of them. Enhancing these systems’ security and shielding them from illegal access and data breaches are the main objectives.
IT workers, security aficionados, and anybody else interested in a career in cybersecurity are the main audiences for these events. Our goal is to provide participants with the information and abilities needed to defend enterprises against online threats and carry out approved penetration tests to improve system security.
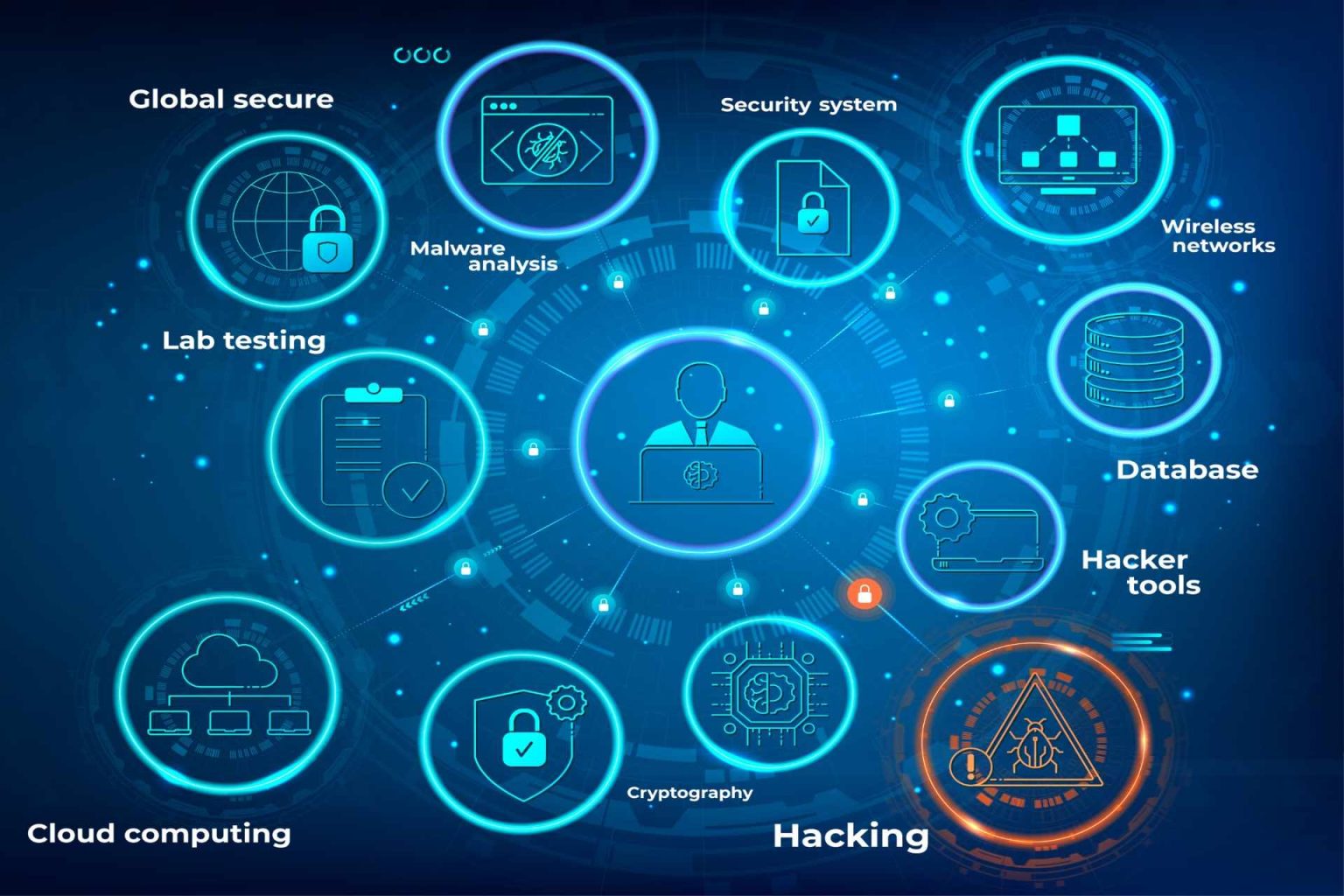
Through the assumption of an attacker’s thinking and toolkit, this program offers the fundamental information required to find and exploit vulnerabilities in systems in an ethical and efficient manner. You can strengthen the security of your company and learn how to safeguard systems by studying how they are attacked. You can also utilize this set of labs and courses to be ready for the Certified Ethical Hacker exams. A wide range of cybersecurity and ethical hacking related subjects are usually covered in the curriculum. These subjects could cover social engineering, malware analysis, network security, online application security, cryptography, and more. Both the theoretical ideas and the useful hacking skills are taught to participants. The optimal way to use Kali Linux and its toolkit for every stage of penetration testing will be covered in this series of courses.

This ethical hacking course will help you
Introduction toEthicalHacking
Reconnaissance/Footprinting
Scanning Networks
Enumeration
Vulnerability Analysis
System Hacking
Malware Threats
Sniffing
Social Engineering
Web Application Hacking
Network and Perimeter Hacking
Hacking Wireless Networks
Hacking Mobile Platforms
Hacking IoT and OT
Cloud Computing
Cryptography

Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Come and discuss your objectives with us.